TakeOver Room
Welcome to the TakeOver Challenge Room on Try Hack Me!
So, it’s important to have your basics regarding certificates and domains clear before starting this room.
Scenario: One of the co-founders of futurevera[.]thm is trying to rebuild their support in order to answer any space-related questions by students.
Recently, blackhat hackers approached them, saying they could take over and are asking them for a big ransom. We need to help the co-founder find what they can take over.
Alright, let’s get started!
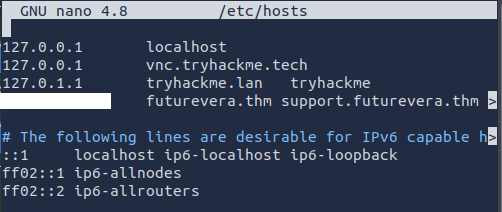
As per the room, we need to add ‘target ip’ in /etc/hosts for futurevera[.]thm
This can be done using the nano /etc/hosts and now you can enter the info and save it.
TASK 1: Help Us
Firstly, to find what the attackers can exploit, we need to have an attacker’s mindset. I began by starting with the first step that any attacker would start with, according to frameworks like MITRE ATT&CK or be it Cyber Kill Chain, i.e, Reconnaissance.
Basically, finding out what all ports and services are open and running. For this, there can be no better tool than Nmap.
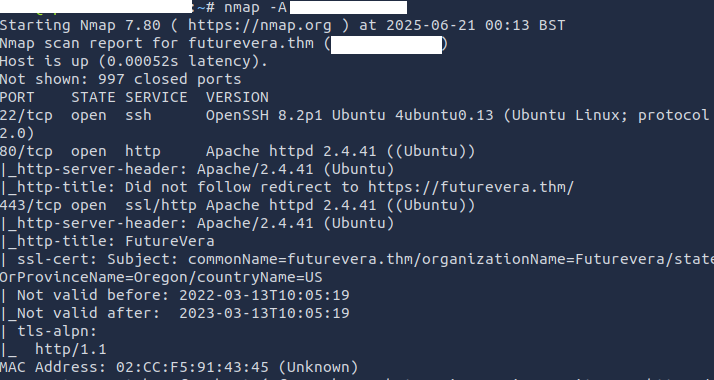
So, I started using the following scan
1
nmap -A 10.10.81.145
-A flag here is used for aggressive scan, providing us with the maximum information that we can get.
Here’s what we found
We see that Port 22, 80 and 443 is open
Furthermore, the certificate being used is an SSL Certificate, and if we carefully observe the dates, then we see it has expired way back in 2023.
Since the room description mentions subdomain enumeration, we need to shift our focus to that, keeping the above info in mind.
Subdomain enumeration is the process of finding subdomains associated with a main domain (like example.com). These subdomains (like admin.example.com, mail.example.com, test.example.com) can reveal hidden services, development environments, or even vulnerable systems that attackers might exploit.
We can find subdomains using various open-source tools available on the internet, be it Fuff, Sublist3r, etc.
See, our last option is to use these tools to get the subdomains. But …
With a bit of attention to detail, we know that the co-founder is working on rebuilding support, then why not give it a shot!
Again, we need to add this to our /etc/host as done before.
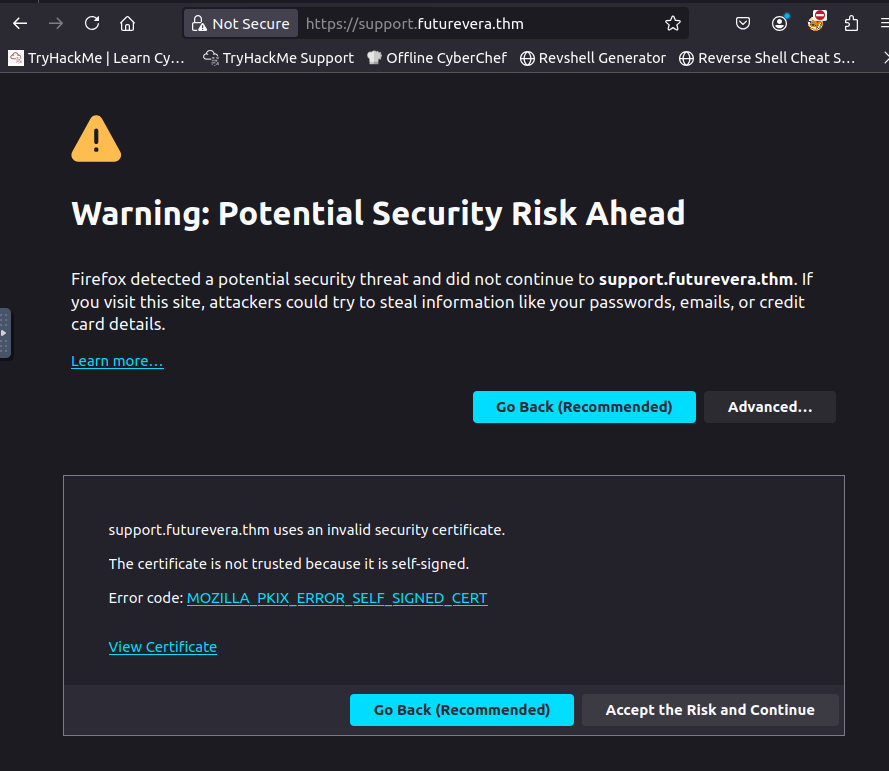
We actually found a subdomain with support!
If we browse this, we get something like this (Obviously, since the certificate is not valid !)
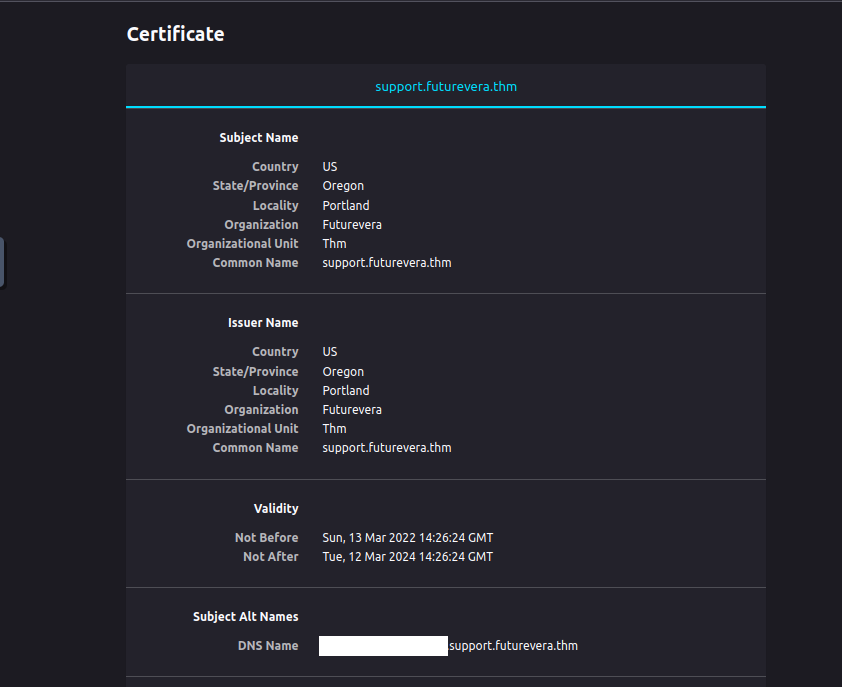
Let’s view the certificate
On inspecting the certificate, I found that it had an alternative DNS Name. So, I tried repeating the same steps that I did for the support subdomain, i.e, to add it to /etc/hosts
On trying to access that particular domain subdomain in the browser, we get our flag displayed right in front of us.